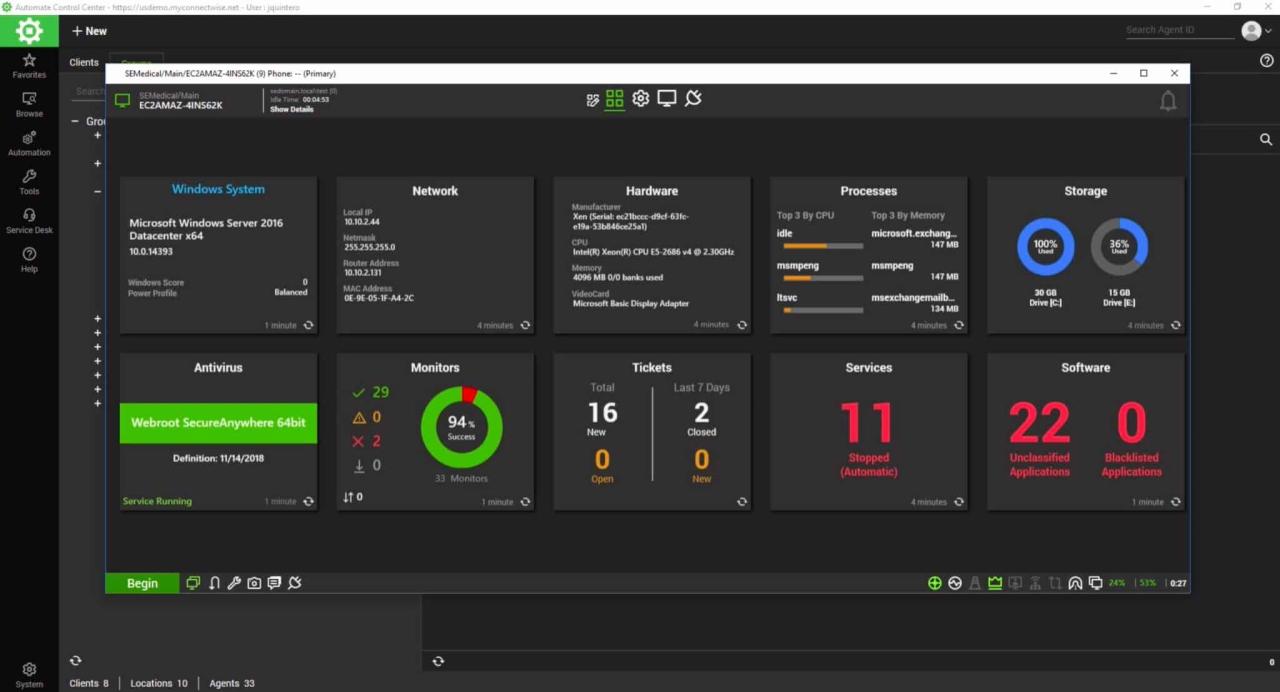
Best RMM software is a vital tool for businesses of all sizes, enabling IT teams to manage and monitor their systems remotely, ensuring optimal performance, security, and efficiency. RMM, or Remote Monitoring and Management, software empowers organizations to proactively address potential issues before they impact operations, leading to improved uptime, reduced downtime, and increased productivity.
Table of Contents
RMM solutions encompass a wide range of features, including remote control, patch management, security monitoring, and reporting. These tools provide a centralized platform for managing endpoints, streamlining IT operations, and reducing the workload of IT staff. From small businesses to large enterprises, RMM software offers a comprehensive approach to managing and optimizing IT infrastructure.
What is RMM Software?
RMM software, short for Remote Monitoring and Management software, is a powerful tool for IT professionals and managed service providers (MSPs) to remotely monitor, manage, and maintain computer systems and networks. It offers a centralized platform to automate tasks, improve efficiency, and ensure the smooth operation of IT infrastructure.
Purpose and Functionality
RMM software is designed to streamline IT operations by providing a comprehensive set of tools and features for managing endpoints, servers, and networks. It enables IT teams to:
- Monitor System Performance: Track key metrics like CPU usage, memory utilization, disk space, and network activity to identify potential performance bottlenecks and proactively address issues.
- Manage Software and Updates: Automate software deployment, patch management, and update distribution to ensure all devices are running the latest and secure versions of software.
- Remotely Access and Control Devices: Gain remote access to workstations and servers, enabling technicians to troubleshoot problems, install software, and perform other tasks remotely.
- Automate Routine Tasks: Schedule and automate repetitive tasks like backups, system scans, and software updates, freeing up IT staff to focus on more strategic initiatives.
- Implement Security Measures: Monitor security events, manage user accounts, and enforce security policies to protect against malware, unauthorized access, and data breaches.
Key Features and Benefits
RMM software offers a wide range of features that can significantly enhance IT operations. Some of the key benefits include:
- Improved Efficiency: Automation of tasks reduces manual effort, allowing IT teams to manage a larger number of devices with fewer resources.
- Enhanced Security: Proactive monitoring and security measures help to identify and mitigate potential threats before they can cause harm.
- Increased Uptime: By proactively monitoring system performance and addressing issues before they become critical, RMM software helps to minimize downtime and maintain business continuity.
- Reduced Costs: Automation and efficiency gains can lead to significant cost savings by reducing the need for on-site support and minimizing downtime.
- Improved Client Satisfaction: Faster resolution times and proactive maintenance improve client satisfaction and build trust in the IT service provider.
Examples of How RMM Software Can Improve IT Operations
RMM software can be applied across various IT scenarios to improve efficiency and security. Here are some examples:
- Proactive Patch Management: An RMM solution can automatically scan for and deploy security patches to all endpoints, ensuring that systems are protected from known vulnerabilities.
- Remote Troubleshooting: In case of a system failure, an IT technician can remotely access the affected device, diagnose the issue, and implement a solution without having to travel on-site.
- Automated Backups: RMM software can schedule and automate backups of critical data, ensuring that data is protected even in the event of a disaster.
- Centralized Security Management: By managing user accounts, enforcing security policies, and monitoring security events from a central console, RMM software helps to streamline security management and improve overall security posture.
Key Features of RMM Software: Best Rmm Software
RMM software offers a wide range of features designed to simplify IT management, enhance security, and improve efficiency. These features are grouped into categories to provide a comprehensive understanding of the capabilities offered by RMM solutions.
Remote Control
Remote control is a fundamental feature of RMM software, allowing IT professionals to access and manage devices remotely. This eliminates the need for physical presence, enabling faster troubleshooting and support.
- Real-time access: RMM software provides immediate access to remote devices, allowing IT teams to view desktops, servers, and other devices in real time.
- Interactive sessions: Remote control enables interactive sessions, allowing technicians to control the mouse and keyboard of a remote device, as if they were physically present.
- File transfer: RMM software facilitates file transfer between the technician’s workstation and the remote device, simplifying the process of installing software, transferring data, or retrieving files.
Patch Management
Patch management is a critical aspect of IT security, ensuring that devices are protected against vulnerabilities and threats. RMM software streamlines the patch management process, reducing the risk of security breaches.
- Automated patch deployment: RMM software automatically identifies and deploys security patches, eliminating manual intervention and ensuring timely updates.
- Patch scheduling: RMM solutions allow IT teams to schedule patch deployments during off-peak hours, minimizing disruption to end-users.
- Vulnerability scanning: RMM software performs vulnerability scans to identify potential security weaknesses and prioritize patch deployments based on severity.
Security
Security is paramount in modern IT environments, and RMM software provides robust security features to protect devices and data.
- Endpoint security: RMM solutions offer endpoint security features, including antivirus protection, firewall management, and intrusion detection, to prevent malware infections and unauthorized access.
- Data encryption: RMM software enables data encryption at rest and in transit, safeguarding sensitive information from unauthorized access.
- Security policies: RMM solutions allow IT teams to implement and enforce security policies, ensuring consistent security measures across all devices.
Reporting
RMM software provides comprehensive reporting capabilities, enabling IT teams to track device health, performance, and security posture.
- Device inventory: RMM software generates reports on the hardware and software inventory of all managed devices, providing valuable insights into the IT infrastructure.
- Performance monitoring: RMM solutions monitor device performance metrics, such as CPU utilization, memory usage, and disk space, identifying potential performance bottlenecks.
- Security audits: RMM software provides security audit reports, highlighting vulnerabilities and security events, enabling proactive security management.
Benefits of Using RMM Software
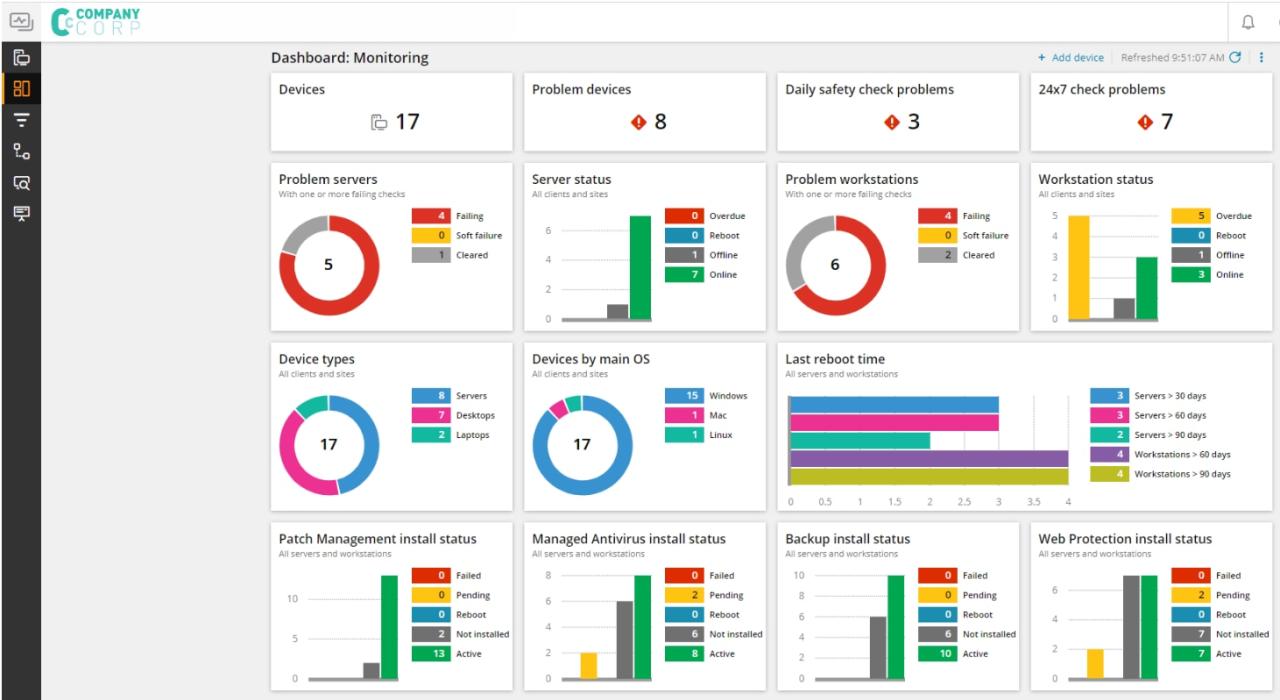
RMM software offers a plethora of advantages for businesses of all sizes, contributing significantly to enhanced productivity, efficiency, and security. By automating routine tasks and providing centralized management capabilities, RMM solutions empower businesses to streamline IT operations, improve resource allocation, and proactively address potential issues before they escalate into major problems.
Enhanced Productivity and Efficiency
RMM software significantly enhances productivity and efficiency by automating routine IT tasks, allowing IT professionals to focus on more strategic initiatives.
- Automated Patch Management: RMM software automates the process of applying software updates and security patches across all devices, ensuring that systems are always up-to-date and protected against vulnerabilities. This eliminates the need for manual patching, saving valuable time and resources.
- Remote Monitoring and Management: RMM solutions enable IT professionals to remotely monitor and manage devices from a centralized dashboard, providing real-time insights into system performance and identifying potential issues before they impact users. This eliminates the need for on-site visits, reducing downtime and improving response times.
- Automated Scripting and Task Scheduling: RMM software allows IT professionals to create and schedule automated scripts for repetitive tasks, such as backups, software installations, and system maintenance. This frees up valuable time and reduces the risk of human error.
Improved Security
RMM software plays a crucial role in enhancing security by providing comprehensive monitoring and control over devices and applications.
- Real-time Threat Detection: RMM solutions monitor devices for suspicious activity and potential security threats, alerting IT professionals to any anomalies that require immediate attention. This allows for proactive threat mitigation and reduces the risk of data breaches.
- Vulnerability Scanning: RMM software automatically scans devices for known vulnerabilities and provides detailed reports, enabling IT professionals to prioritize remediation efforts and strengthen overall security posture.
- Endpoint Security Management: RMM solutions provide centralized control over endpoint security settings, allowing IT professionals to enforce consistent security policies across all devices. This reduces the risk of unauthorized access and data breaches.
Cost Savings
RMM software can significantly reduce IT costs by streamlining operations, improving efficiency, and minimizing downtime.
- Reduced IT Staff Requirements: RMM solutions automate many routine tasks, freeing up IT staff to focus on more strategic initiatives. This can potentially reduce the need for additional IT personnel, leading to cost savings.
- Minimized Downtime: RMM software enables proactive monitoring and management, allowing IT professionals to identify and resolve issues before they impact users. This minimizes downtime and reduces the associated costs of lost productivity.
- Improved Resource Allocation: RMM solutions provide real-time insights into system performance and resource utilization, enabling IT professionals to optimize resource allocation and reduce unnecessary expenses.
Choosing the Right RMM Software
Selecting the best RMM software for your organization is crucial for streamlining IT operations, improving efficiency, and ensuring robust security. The right solution can significantly impact your ability to manage devices, deploy updates, monitor performance, and respond to incidents effectively.
Factors to Consider When Choosing RMM Software
When choosing RMM software, several key factors should be considered to ensure a solution that aligns with your specific needs and requirements. These factors can help you make an informed decision that leads to improved IT management and enhanced business outcomes.
- Scalability: Choose software that can adapt to your organization’s growth, allowing you to manage a larger number of devices and users without compromising performance.
- Features: Identify the specific features you require, such as remote access, patch management, endpoint security, and reporting. Ensure the software provides the necessary tools to meet your IT management goals.
- Pricing: Evaluate different pricing models, including per-device, per-technician, or flat-fee subscriptions. Choose a pricing structure that aligns with your budget and the size of your IT environment.
- Ease of Use: Select software with a user-friendly interface that is easy for your IT team to learn and use. This ensures a smooth transition and minimizes training requirements.
- Security: Prioritize RMM software with robust security features, including encryption, multi-factor authentication, and regular security updates. This protects your data and devices from unauthorized access and cyber threats.
- Customer Support: Look for software providers that offer responsive and reliable customer support. This is essential for addressing technical issues, resolving problems, and receiving assistance when needed.
- Integrations: Assess the software’s compatibility with existing IT infrastructure and systems, including help desk software, monitoring tools, and security solutions. Seamless integration ensures a cohesive IT management environment.
Comparing RMM Software Solutions
To help you choose the right RMM software, consider the following table comparing key features, pricing, and compatibility of popular solutions. This comparison provides a starting point for evaluating different options based on your specific needs.
| Software | Features | Pricing | Compatibility |
|---|---|---|---|
| Atera | Remote access, patch management, endpoint security, ticketing system, reporting | Starts at $79 per month | Windows, macOS, Linux |
| ConnectWise Automate | Remote access, patch management, endpoint security, scripting, automation | Starts at $149 per month | Windows, macOS, Linux |
| Datto RMM | Remote access, patch management, endpoint security, backup and recovery, disaster recovery | Starts at $199 per month | Windows, macOS, Linux |
| NinjaOne | Remote access, patch management, endpoint security, asset management, IT documentation | Starts at $59 per month | Windows, macOS, Linux |
| SolarWinds N-central | Remote access, patch management, endpoint security, network monitoring, server management | Starts at $199 per month | Windows, macOS, Linux |
Compatibility with Existing IT Infrastructure
Compatibility with existing IT infrastructure is crucial for a smooth transition and to avoid conflicts or issues with existing systems. Choose RMM software that integrates seamlessly with your current tools and platforms. For example, if you use a specific ticketing system, ensure the RMM software can integrate with it for a unified workflow.
“Ensure the RMM software you choose is compatible with your existing IT infrastructure and systems to avoid potential conflicts and ensure a smooth transition.”
RMM Software for Different Business Needs
RMM software can be tailored to meet the specific needs of various industries and business sizes. The features and functionalities of RMM solutions can be customized to address the unique challenges and requirements of different sectors.
RMM Software for Healthcare
Healthcare organizations face unique challenges in managing IT infrastructure, including compliance with regulations like HIPAA and ensuring patient data security. RMM software specifically designed for healthcare can help meet these challenges by providing:
- HIPAA-compliant security features: This includes encryption, access controls, and auditing capabilities to protect sensitive patient information.
- Automated patch management: RMM software can automatically update systems with the latest security patches, reducing the risk of vulnerabilities and breaches.
- Remote monitoring and management: This allows healthcare providers to monitor and manage devices remotely, reducing downtime and ensuring continuity of care.
RMM Software for Education, Best rmm software
Educational institutions face the challenge of managing a large number of devices, often spread across multiple locations. RMM software can help streamline IT management by:
- Centralized device management: RMM software allows IT teams to manage all devices from a single console, simplifying administration and reducing workload.
- Automated software deployment: This enables schools to quickly and efficiently deploy software updates and applications to all devices.
- Remote troubleshooting: IT staff can remotely diagnose and resolve technical issues on student and faculty devices, minimizing downtime and disruptions.
RMM Software for Finance
Financial institutions have strict security and compliance requirements. RMM software tailored for finance can help meet these requirements by:
- Advanced security features: This includes multi-factor authentication, intrusion detection, and data loss prevention to protect sensitive financial data.
- Compliance reporting: RMM software can generate reports that demonstrate compliance with industry regulations like PCI DSS.
- Disaster recovery and business continuity: RMM solutions can help ensure business continuity in the event of a disaster by providing automated backup and recovery capabilities.
RMM Software Deployment and Implementation
Getting your chosen RMM software up and running effectively involves a series of well-defined steps. This process, known as deployment and implementation, ensures that your software is integrated seamlessly into your existing IT infrastructure and delivers the desired benefits.
Deployment Steps
The deployment of RMM software typically follows a structured approach, encompassing these key steps:
- Initial Assessment: Before starting, assess your existing IT environment, including the number of devices, operating systems, and any existing security solutions. This will help you determine the appropriate RMM software features and functionalities.
- Software Installation: Install the RMM software on your central server or cloud platform. This usually involves downloading the software, configuring it according to your needs, and setting up the initial network connection.
- Agent Deployment: Install the RMM agent on each endpoint device (computers, laptops, servers) that you want to manage. This agent is responsible for collecting data and executing commands from the central server.
- Configuration and Customization: Configure the RMM software to align with your specific requirements. This might include setting up policies, defining user roles, and customizing alerts and reports.
- Testing and Validation: After deployment, thoroughly test the RMM software to ensure it functions as expected. Run simulations to validate its ability to monitor, manage, and secure your endpoints.
- Go Live: Once satisfied with the testing, you can fully integrate the RMM software into your IT environment. This may involve migrating existing management tasks from other tools to the new RMM platform.
Training and Support
Providing adequate training and support to users is crucial for successful RMM implementation.
- User Training: Offer comprehensive training to your IT team on how to use the RMM software effectively. This training should cover essential functionalities, reporting tools, and troubleshooting techniques.
- Documentation and Resources: Provide easily accessible documentation, tutorials, and online resources to assist users in navigating the RMM software.
- Ongoing Support: Offer ongoing technical support to address any user queries, troubleshoot issues, and ensure the RMM software remains operational.
Best Practices for Successful Implementation
To maximize the benefits of RMM software, consider these best practices:
- Clear Objectives: Define clear objectives for implementing the RMM software. What specific IT management challenges do you aim to address? This clarity will guide your deployment process and ensure alignment with your goals.
- Pilot Testing: Before full deployment, consider conducting a pilot test with a smaller group of devices or users. This allows you to identify potential issues and refine the implementation process.
- Phased Rollout: Instead of deploying the RMM software to all devices at once, consider a phased rollout. This allows for gradual testing, reduces potential disruptions, and facilitates user acclimation.
- Regular Monitoring: Monitor the RMM software’s performance regularly to ensure it’s meeting your needs. Identify any performance bottlenecks or areas for improvement and make necessary adjustments.
- User Feedback: Actively seek user feedback to understand their experiences with the RMM software. This feedback can help identify areas for improvement and enhance user satisfaction.
Security Considerations with RMM Software

RMM software offers numerous benefits for IT management, but it also presents certain security considerations that require careful attention. This section delves into the security implications of using RMM software, exploring how it can enhance endpoint security and data protection while identifying potential risks.
Endpoint Security Enhancement
RMM software significantly enhances endpoint security by providing centralized control and automation for various security measures.
- Patch Management: RMM software automates the process of installing security patches and updates across all managed endpoints, ensuring systems are protected against known vulnerabilities.
- Antivirus and Malware Protection: RMM software can manage and monitor antivirus and anti-malware solutions, ensuring they are up-to-date and effectively protecting endpoints from threats.
- Firewall Configuration: RMM software allows administrators to configure and manage firewalls on managed devices, controlling network traffic and preventing unauthorized access.
- Security Policy Enforcement: RMM software enforces security policies across endpoints, such as password complexity requirements, data encryption, and access control settings, ensuring consistent security standards.
Data Protection Measures
RMM software plays a crucial role in protecting sensitive data stored on managed endpoints.
- Data Encryption: RMM software can enforce data encryption policies, ensuring that sensitive data is protected even if devices are lost or stolen.
- Data Backup and Recovery: RMM software facilitates regular data backups, allowing for quick and reliable data recovery in case of data loss or corruption.
- Data Loss Prevention: RMM software can implement data loss prevention (DLP) measures, preventing sensitive data from leaving the organization’s network without authorization.
Potential Security Risks
While RMM software offers numerous security benefits, it also introduces potential security risks that need to be addressed.
- Unauthorized Access: If the RMM software itself is compromised, attackers could gain access to managed endpoints and sensitive data. Strong authentication measures and access control mechanisms are essential to mitigate this risk.
- Data Breaches: RMM software stores and transmits sensitive data, making it a potential target for data breaches. Implementing robust security measures, such as encryption and secure communication protocols, is crucial for protecting data integrity.
- Malicious Software: RMM software can be a vector for malicious software if it is not properly secured. Regularly updating the software and implementing security best practices can help prevent this risk.
- Misconfiguration: Incorrectly configured RMM software can expose managed endpoints to vulnerabilities. It is essential to carefully configure and test the software to ensure it is properly secured.
Security Best Practices
To mitigate security risks associated with RMM software, organizations should adopt the following best practices:
- Choose a reputable RMM vendor: Select an RMM vendor with a proven track record of security and compliance.
- Implement strong authentication: Use multi-factor authentication (MFA) for accessing the RMM console and manage user permissions carefully.
- Keep the software up-to-date: Regularly update the RMM software and all associated components to patch vulnerabilities.
- Monitor security logs: Actively monitor security logs for any suspicious activity and investigate any anomalies promptly.
- Conduct regular security audits: Perform regular security audits to assess the effectiveness of security controls and identify any vulnerabilities.
RMM Software Integration and Automation
RMM software goes beyond simply managing endpoints. It excels at integrating with other IT tools and services, enabling seamless workflows and automation for various IT tasks. This integration capability significantly streamlines IT operations, saving time, effort, and resources.
Integration Capabilities of RMM Software
RMM software offers a wide range of integration capabilities, allowing it to connect with various IT tools and services. This interconnectedness enables data sharing, task synchronization, and enhanced functionality.
- Ticketing Systems: Integration with ticketing systems like Zendesk, Jira, or Freshdesk allows IT teams to automatically create tickets within the RMM software when specific events occur, such as a device failure or security alert. This ensures seamless communication and tracking of issues.
- Monitoring Tools: Integration with monitoring tools like Datadog, New Relic, or Prometheus allows RMM software to collect and analyze data from various sources, providing a comprehensive view of IT infrastructure health and performance. This integration helps proactively identify potential issues and optimize system performance.
- Backup and Recovery Solutions: Integration with backup and recovery solutions like Veeam, Acronis, or Carbonite enables RMM software to automatically trigger backups and restore data in case of system failures. This ensures data protection and business continuity in the event of unforeseen circumstances.
- Security Information and Event Management (SIEM): Integration with SIEM solutions like Splunk, AlienVault, or LogRhythm allows RMM software to share security events and logs with the SIEM system for centralized analysis and threat detection. This integration enhances security posture and incident response capabilities.
- Remote Desktop Software: Integration with remote desktop software like TeamViewer, LogMeIn, or Splashtop enables technicians to remotely access and manage endpoints from anywhere, improving troubleshooting and support efficiency.
Automating Repetitive Tasks and Processes
RMM software can automate various repetitive tasks and processes, freeing up IT teams to focus on more strategic initiatives.
- Patch Management: RMM software can automatically scan endpoints for missing patches, download and install updates, and report on patch compliance. This ensures timely security updates and reduces vulnerability risks.
- Software Deployment: RMM software can automatically deploy software applications to endpoints, eliminating the need for manual installation and configuration. This streamlines software distribution and reduces deployment time.
- Script Execution: RMM software can execute predefined scripts on endpoints, automating routine tasks like system maintenance, configuration changes, or data collection. This reduces manual intervention and ensures consistent task execution.
- Asset Management: RMM software can automatically discover and inventory hardware and software assets, providing a comprehensive view of IT infrastructure. This information can be used for asset management, capacity planning, and compliance reporting.
- Reporting and Analytics: RMM software can generate automated reports and dashboards, providing insights into IT infrastructure health, performance, and security. This data can be used to make informed decisions and optimize IT operations.
Benefits of Automating IT Operations
Automating IT operations using RMM software offers numerous benefits, including:
- Increased Efficiency: Automation reduces manual effort and streamlines IT processes, freeing up IT teams to focus on more strategic tasks.
- Reduced Errors: Automation minimizes human error and ensures consistency in task execution, improving accuracy and reliability.
- Improved Security: Automation helps ensure timely security updates, vulnerability patching, and incident response, enhancing overall security posture.
- Enhanced Productivity: Automation streamlines IT operations, reducing downtime and improving service delivery, resulting in increased productivity.
- Cost Savings: Automation reduces the need for manual intervention, saving time and resources, and potentially lowering operational costs.
RMM Software Pricing and Licensing Models
RMM software pricing can vary significantly depending on the provider, features offered, and the number of devices managed. Understanding the different pricing models and factors influencing pricing is crucial for choosing a cost-effective solution that meets your specific needs.
Pricing Models
RMM software providers typically offer a variety of pricing models, each with its own advantages and disadvantages. The most common pricing models include:
- Per-device pricing: This model charges a fixed fee per device managed. It is a straightforward and predictable pricing model, making it easy to estimate costs. However, it can become expensive for businesses managing a large number of devices.
- Per-technician pricing: This model charges a fee based on the number of technicians using the software. It is a suitable option for businesses with a small team of IT professionals. However, it may not be cost-effective for businesses with a large number of technicians.
- Subscription-based pricing: This model charges a recurring monthly or annual fee for access to the software. It provides predictable costs and often includes updates and support. Subscription-based pricing can be more cost-effective in the long run, especially for businesses with growing device counts.
- Tiered pricing: This model offers different pricing tiers based on the features and functionality included. Lower tiers typically offer basic features, while higher tiers include advanced features. This model allows businesses to choose a plan that best suits their needs and budget.
Factors Influencing RMM Software Pricing
Several factors influence RMM software pricing, including:
- Features: RMM software with more advanced features, such as remote control, patch management, and endpoint security, typically costs more.
- Number of devices: The number of devices managed is a significant factor in pricing. As the number of devices increases, the cost of the software generally increases.
- Support: Providers offering 24/7 support or premium support options may charge a higher price.
- Integrations: Software with integrations with other tools and services may cost more.
Choosing a Cost-Effective RMM Software Solution
When choosing an RMM software solution, consider the following factors to ensure a cost-effective choice:
- Determine your specific needs: Identify the features and functionality you require based on your business size, device count, and IT support needs.
- Compare pricing models: Analyze the different pricing models offered by different providers and choose the model that best aligns with your budget and device count.
- Look for value-added features: Consider features that can save you time and resources, such as automated patch management, remote control, and reporting.
- Negotiate pricing: Don’t hesitate to negotiate with providers, especially if you have a large device count or require specific features.
Recommendations for Cost-Effective RMM Software Solutions
Here are some recommendations for choosing cost-effective RMM software solutions:
- Consider cloud-based solutions: Cloud-based RMM software typically has lower upfront costs and requires less hardware investment.
- Look for providers with flexible pricing models: Choose providers that offer per-device, per-technician, or tiered pricing models to find a plan that suits your budget.
- Start with a small plan and scale up as needed: If you are unsure about your needs, start with a small plan and upgrade as your business grows.
- Look for free trials or demos: This allows you to test the software and ensure it meets your needs before committing to a subscription.
Future Trends in RMM Software
The RMM software market is constantly evolving, driven by technological advancements, changing business needs, and the increasing demand for robust security solutions. As we look ahead, several key trends are shaping the future of RMM software, promising to enhance efficiency, security, and user experience.
Integration with Artificial Intelligence (AI) and Machine Learning (ML)
AI and ML are poised to revolutionize RMM software, bringing about significant improvements in automation, predictive maintenance, and threat detection. RMM solutions are increasingly incorporating AI and ML algorithms to automate repetitive tasks, such as patch management and software updates. AI-powered predictive analytics can analyze historical data to identify potential issues before they arise, allowing IT teams to proactively address problems and prevent downtime. Additionally, AI-driven threat detection systems can analyze network traffic and identify suspicious activities, providing real-time alerts and helping to prevent cyberattacks.
Enhanced Security Features
As cyber threats become more sophisticated, RMM software is evolving to provide enhanced security features. Advanced endpoint security solutions, such as next-generation antivirus (NGAV) and endpoint detection and response (EDR), are being integrated into RMM platforms. These technologies offer real-time threat detection, behavioral analysis, and automated incident response capabilities. RMM solutions are also incorporating multi-factor authentication (MFA) and encryption technologies to protect sensitive data and ensure secure access to devices.
Cloud-Based RMM Solutions
The adoption of cloud computing is driving the shift towards cloud-based RMM solutions. Cloud-based RMM platforms offer several advantages, including scalability, accessibility, and cost-effectiveness. They allow IT teams to manage devices from anywhere with an internet connection, eliminating the need for on-premises infrastructure. Cloud-based RMM solutions also provide centralized data storage and backups, ensuring data security and disaster recovery.
Remote Work Support
The rise of remote work has significantly impacted the IT landscape, requiring RMM software to adapt and support distributed workforces. RMM solutions are now incorporating features that enable seamless remote device management, including remote access, remote monitoring, and remote troubleshooting. They also provide secure communication channels for remote employees, ensuring data privacy and compliance with regulatory requirements.
Focus on User Experience
RMM software is becoming more user-friendly and intuitive, aiming to simplify IT management for both technical and non-technical users. Modern RMM platforms offer intuitive dashboards, customizable reporting, and simplified workflows. They also provide user-friendly interfaces that allow non-technical personnel to perform basic tasks, such as password resets and software installations.
Epilogue
Choosing the right RMM software requires careful consideration of factors such as features, pricing, compatibility, and scalability. By implementing a robust RMM solution, businesses can gain a significant advantage in today’s digital landscape, ensuring their IT infrastructure remains secure, efficient, and resilient.
Choosing the best RMM software for your business can be a daunting task, but it’s crucial for maintaining optimal system performance and security. You might be surprised to learn that the Tinkercad download can be a valuable tool for visualizing network configurations and understanding complex IT infrastructure, which can help you make informed decisions about your RMM needs.