Remote monitoring & management software has revolutionized the way businesses manage their IT infrastructure. This powerful technology enables organizations to remotely monitor and control their systems, devices, and applications, ensuring optimal performance, security, and efficiency.
Table of Contents
By leveraging remote monitoring and management software, businesses can gain real-time insights into their IT environment, proactively identify and address potential issues, and optimize resource allocation. This approach not only reduces downtime and operational costs but also enhances security by detecting and mitigating threats before they escalate.
What is Remote Monitoring & Management Software?
Remote monitoring and management (RMM) software is a powerful tool that enables businesses to remotely monitor and manage their IT infrastructure, devices, and applications. This software provides a centralized platform for managing all aspects of IT operations, from network monitoring and security to software updates and user management.
Key Functionalities and Features
RMM software offers a comprehensive suite of features designed to streamline IT operations and improve efficiency. Here are some of the key functionalities:
- Network Monitoring: RMM software provides real-time monitoring of network performance, identifying potential issues and bottlenecks before they impact users. This includes monitoring bandwidth usage, network traffic patterns, and device connectivity.
- Security Monitoring and Management: RMM software helps businesses proactively identify and mitigate security threats. This includes monitoring for malware, vulnerabilities, and unauthorized access attempts, and implementing security policies to protect sensitive data.
- Device Management: RMM software allows IT administrators to remotely manage and control devices, including desktops, laptops, servers, and mobile devices. This includes tasks like installing software updates, configuring device settings, and troubleshooting technical issues.
- Software Deployment and Patching: RMM software streamlines the process of deploying software updates and patches across the entire IT infrastructure. This ensures that all devices are running the latest versions of software, minimizing security vulnerabilities and improving performance.
- User Management: RMM software simplifies user account management, including creating new accounts, assigning permissions, and resetting passwords. This helps to maintain control over access to sensitive data and resources.
- Reporting and Analytics: RMM software provides detailed reports and analytics on various aspects of IT infrastructure performance, security, and user activity. This data can be used to identify trends, improve decision-making, and optimize IT operations.
Benefits of Using RMM Software
RMM software offers numerous benefits for businesses of all sizes, helping them to optimize their IT operations and achieve greater efficiency. Some of the key benefits include:
- Reduced IT Costs: RMM software helps to reduce IT costs by automating tasks, minimizing downtime, and preventing issues before they escalate. This frees up IT staff to focus on strategic initiatives and projects.
- Improved Security: RMM software provides comprehensive security monitoring and management, helping businesses to proactively identify and mitigate security threats. This reduces the risk of data breaches and other security incidents.
- Enhanced Productivity: By automating tasks and resolving issues quickly, RMM software helps to improve user productivity and minimize downtime. This allows employees to focus on their core tasks and achieve higher levels of performance.
- Increased Visibility and Control: RMM software provides a centralized platform for managing all aspects of IT infrastructure, giving businesses greater visibility and control over their IT environment. This helps to ensure that all devices and applications are functioning properly and securely.
- Improved Scalability: RMM software is designed to scale with the needs of businesses, allowing them to easily manage growing IT infrastructures. This ensures that IT operations can keep pace with business growth and evolving technology requirements.
Types of Remote Monitoring & Management Software
Remote monitoring and management (RMM) software comes in various forms, each designed to address specific needs and cater to different IT environments. These tools can be categorized based on their functionality, target audience, and the range of services they provide.
Types of Remote Monitoring & Management Software
The types of RMM software can be categorized based on their core functionality and target audience. Here are some common categories:
- Endpoint Management: These tools focus on managing and securing individual computers and devices within a network. They offer features like software deployment, patch management, remote control, and security monitoring. Examples include Datto RMM, Kaseya, and ConnectWise Automate.
- Network Monitoring: Network monitoring RMM software specializes in observing and analyzing network performance, identifying potential issues, and ensuring network uptime. They typically monitor key metrics like bandwidth usage, latency, and device availability. Examples include SolarWinds Network Performance Monitor, ManageEngine OpManager, and PRTG Network Monitor.
- Server Management: Server management RMM tools are designed to monitor and manage servers, including physical and virtual servers. They offer features like server health monitoring, performance optimization, and automated maintenance tasks. Examples include Datto RMM, Atera, and N-able.
- Cloud Management: As cloud adoption increases, cloud management RMM software has emerged to monitor and manage cloud infrastructure, including virtual machines, databases, and applications hosted in cloud environments. Examples include CloudHealth by VMware, AWS CloudTrail, and Azure Monitor.
- Security Monitoring: Security monitoring RMM software prioritizes security and threat detection. They monitor for malware, vulnerabilities, and suspicious activities, providing alerts and incident response capabilities. Examples include Sophos Central, SentinelOne, and CrowdStrike Falcon.
Features and Benefits of Different Types of RMM Software
Each type of RMM software offers unique features and benefits, catering to specific needs.
- Endpoint Management: These tools provide comprehensive control over endpoints, enabling efficient software deployment, patch management, and security updates. They also facilitate remote access and troubleshooting, reducing the need for on-site visits. For example, Datto RMM allows for automated patch management, reducing the risk of security vulnerabilities.
- Network Monitoring: Network monitoring RMM software provides real-time insights into network performance, enabling proactive identification and resolution of issues. This can significantly reduce downtime and improve network reliability. For example, SolarWinds Network Performance Monitor can identify network bottlenecks and optimize performance.
- Server Management: Server management RMM tools offer centralized monitoring and management of servers, simplifying administration and reducing the risk of outages. They automate routine maintenance tasks, saving time and resources. For example, Atera can automate server backups and ensure data integrity.
- Cloud Management: Cloud management RMM software enables efficient management of cloud resources, ensuring optimal performance, security, and cost optimization. They provide visibility into cloud usage and identify potential cost savings. For example, CloudHealth by VMware offers comprehensive cost management and optimization features.
- Security Monitoring: Security monitoring RMM software plays a crucial role in protecting networks and devices from threats. They detect and respond to security incidents, minimizing damage and ensuring data integrity. For example, Sophos Central offers real-time threat detection and response capabilities.
Key Features of Remote Monitoring & Management Software
Remote monitoring and management (RMM) software offers a comprehensive suite of tools designed to streamline IT operations, enhance security, and optimize system performance. These features empower businesses to proactively manage their IT infrastructure, ensuring smooth operations and mitigating potential issues before they impact productivity.
Essential Features of Remote Monitoring & Management Software
Remote monitoring and management software is packed with essential features that work together to enhance system performance and security.
| Feature Name | Description | Benefits |
|---|---|---|
| Remote Access | Allows administrators to connect to and control devices remotely, providing on-demand access to resolve issues and perform maintenance tasks. | Reduces the need for on-site visits, saving time and costs. Enables quick troubleshooting and resolution of issues, minimizing downtime. |
| System Monitoring | Continuously monitors key system metrics, including CPU usage, memory utilization, disk space, and network activity, to identify potential problems before they become critical. | Proactive identification and resolution of performance bottlenecks, preventing system crashes and ensuring optimal resource utilization. Early detection of security threats and anomalies, enabling timely intervention. |
| Patch Management | Automates the process of applying software updates and security patches to all devices, ensuring systems are protected against vulnerabilities. | Reduces the risk of security breaches by eliminating outdated software and vulnerabilities. Streamlines the patching process, saving time and resources. |
| Backup and Recovery | Provides automated data backup and disaster recovery capabilities, ensuring data protection and business continuity in the event of system failures or data loss. | Minimizes data loss and downtime in case of hardware failures, natural disasters, or cyberattacks. Enables quick restoration of systems and data, minimizing business disruption. |
| Security Management | Offers features like endpoint security, antivirus protection, firewall management, and intrusion detection to protect devices and networks from cyber threats. | Enhances overall security posture, reducing the risk of malware infections, data breaches, and unauthorized access. Provides real-time threat detection and response capabilities. |
| Reporting and Analytics | Generates detailed reports and insights into system performance, security events, and user activity, providing valuable data for informed decision-making. | Identifies trends and patterns, enabling proactive optimization of IT infrastructure. Supports compliance audits and reporting requirements. |
Benefits of Implementing Remote Monitoring & Management Software
Remote monitoring and management (RMM) software offers a range of benefits for businesses of all sizes, enabling them to optimize their IT infrastructure, enhance security, and boost productivity. By providing centralized control and automation, RMM software streamlines IT operations, reduces administrative overhead, and improves overall efficiency.
Impact on IT Infrastructure
RMM software simplifies IT infrastructure management by providing a comprehensive view of all devices and systems within an organization. This centralized platform allows IT professionals to monitor system performance, identify potential issues, and proactively address them before they escalate into major problems. The ability to remotely access and manage devices significantly reduces the need for on-site visits, saving time and resources.
- Improved System Performance: RMM software helps identify performance bottlenecks and optimize resource allocation, ensuring smooth operation of critical systems. For instance, by monitoring CPU usage and memory consumption, IT teams can identify and address resource-intensive applications that may be impacting overall performance.
- Enhanced Security Posture: RMM software provides robust security features, such as vulnerability scanning, patch management, and endpoint security. By proactively identifying and addressing security vulnerabilities, organizations can significantly reduce their risk of cyberattacks. For example, automated patch management ensures that systems are always up-to-date with the latest security updates, minimizing the potential for exploitation by malicious actors.
- Simplified Device Management: RMM software simplifies the management of diverse IT devices, including computers, servers, and mobile devices. IT professionals can remotely deploy software updates, configure settings, and troubleshoot issues, regardless of the device’s physical location. This centralized management approach reduces administrative burden and improves efficiency.
Impact on Security
RMM software plays a critical role in bolstering an organization’s security posture. By providing real-time monitoring, automated threat detection, and proactive security measures, RMM software helps organizations mitigate cyber risks and protect sensitive data.
- Real-Time Threat Detection: RMM software continuously monitors network traffic and system activity for suspicious patterns and anomalies. This real-time threat detection allows IT teams to quickly identify and respond to potential security incidents, minimizing the impact of attacks. For example, RMM software can detect malware infections, unauthorized access attempts, and other suspicious activities, enabling prompt remediation.
- Automated Security Measures: RMM software automates security tasks, such as patch management, antivirus updates, and firewall configuration. This automation ensures that security measures are consistently applied across all devices, reducing the risk of vulnerabilities and enhancing overall security. For instance, automated patch management ensures that systems are always up-to-date with the latest security updates, minimizing the potential for exploitation by malicious actors.
- Data Backup and Recovery: RMM software facilitates data backup and recovery, ensuring that critical data is protected in case of system failures or cyberattacks. This capability allows organizations to quickly restore data and minimize downtime in the event of an incident. For example, RMM software can automatically back up data to secure off-site locations, providing a reliable recovery mechanism in case of disaster.
Impact on Productivity
RMM software empowers businesses to enhance productivity by streamlining IT operations, reducing downtime, and improving collaboration. This translates into increased efficiency, better resource utilization, and a more productive workforce.
- Reduced Downtime: RMM software proactively identifies and resolves IT issues, minimizing downtime and maximizing productivity. By detecting problems early and implementing timely solutions, organizations can avoid disruptions to critical business operations. For example, RMM software can monitor system performance and automatically restart services or applications that are experiencing issues, ensuring continuous operation.
- Improved Collaboration: RMM software facilitates collaboration between IT professionals and end-users. IT teams can remotely access and manage devices, resolve issues quickly, and provide technical support without the need for on-site visits. This improved communication and collaboration enhance productivity and user satisfaction.
- Automated Task Management: RMM software automates repetitive IT tasks, freeing up IT professionals to focus on more strategic initiatives. This automation improves efficiency, reduces administrative overhead, and allows IT teams to dedicate their time to more complex and value-adding activities. For example, RMM software can automate tasks such as software deployment, patch management, and system updates, reducing the workload on IT professionals.
Benefits in Different Business Scenarios
| Business Scenario | Benefits |
|---|---|
| Small Businesses | – Reduced IT costs through remote management and support – Enhanced security with automated threat detection and prevention – Improved productivity with streamlined IT operations |
| Medium Businesses | – Centralized control and visibility over IT infrastructure – Scalable platform to manage growing IT needs – Improved collaboration and communication between IT and users |
| Large Enterprises | – Comprehensive IT management across multiple locations – Automated compliance and regulatory reporting – Proactive monitoring and incident response to minimize downtime |
How to Choose the Right Remote Monitoring & Management Software
Choosing the right remote monitoring and management (RMM) software can be a daunting task, as there are numerous options available with varying features and pricing. To make the process smoother, it’s essential to have a clear understanding of your requirements and follow a structured approach to selecting the best solution for your needs.
Factors to Consider
The selection process involves carefully evaluating several factors to ensure the chosen software aligns with your organization’s specific needs and budget.
- Budget: Determine your budget for RMM software and consider the costs associated with implementation, training, and ongoing support. Look for solutions that offer flexible pricing models and transparent cost structures.
- Scalability: Choose software that can scale with your business growth. Consider the number of devices you need to manage, the anticipated increase in users, and the potential expansion of your IT infrastructure.
- Compatibility: Ensure the RMM software is compatible with your existing IT infrastructure, including operating systems, hardware, and other software applications. Compatibility issues can lead to integration problems and increased downtime.
- Features: Identify the essential features you require in an RMM solution, such as remote access, patch management, endpoint security, and reporting. Prioritize features based on your specific needs and prioritize the most important ones.
- Ease of Use: Opt for software with a user-friendly interface that is easy to navigate and understand. A straightforward interface minimizes training time and ensures efficient use by your IT team.
- Security: Security is paramount when choosing RMM software. Ensure the software utilizes robust security measures, such as encryption and multi-factor authentication, to protect sensitive data and prevent unauthorized access.
- Support: Evaluate the level of support offered by the software vendor. Look for options that provide 24/7 support, comprehensive documentation, and regular updates to ensure ongoing assistance and timely resolution of issues.
- Customer Reviews: Research user reviews and testimonials from other organizations that have implemented the RMM software. These reviews can provide valuable insights into the software’s performance, reliability, and customer satisfaction.
Questions to Ask Potential Software Providers
Before making a final decision, it’s crucial to ask potential software providers specific questions to gain a comprehensive understanding of their solutions and ensure they meet your requirements.
- What are the key features and benefits of your RMM software?
- How does your software handle different operating systems and devices?
- What security measures are in place to protect data and prevent unauthorized access?
- What is the pricing model, and are there any hidden costs or fees?
- What level of support is provided, and what are the response times for technical issues?
- Can you provide case studies or testimonials from other organizations using your software?
- What is the process for onboarding and training new users?
- How often are software updates and patches released?
- What are the system requirements for your software?
Trial Period
Request a free trial of the software to evaluate its functionality and usability firsthand. This allows you to test the software in a real-world environment and assess its suitability for your specific needs.
Demo
Schedule a demo with the software vendor to get a personalized demonstration of the RMM software’s features and capabilities. This provides an opportunity to ask questions and gain a deeper understanding of the software’s functionality.
Implementing Remote Monitoring & Management Software
Implementing remote monitoring and management (RMM) software involves a series of steps to ensure a smooth transition and effective utilization. This process involves careful planning, configuration, and integration with your existing IT infrastructure.
Planning for Implementation
Before diving into the technical aspects, it’s crucial to have a clear plan in place. This plan should Artikel the goals you aim to achieve with RMM software, identify the specific functionalities required, and determine the scope of implementation.
- Define Objectives: Clearly define your goals for implementing RMM software. Are you looking to improve security, streamline IT management, reduce downtime, or enhance remote support capabilities? Establishing specific objectives will guide your implementation process and ensure you select the right features and functionalities.
- Identify Key Stakeholders: Involve relevant stakeholders, including IT personnel, management, and end-users, in the planning process. This collaborative approach ensures that everyone understands the benefits of RMM software and their role in the implementation.
- Assess Existing IT Infrastructure: Before implementing RMM software, evaluate your existing IT infrastructure. This includes understanding your network architecture, device types, and existing security measures. This assessment will help you determine compatibility and potential integration challenges.
- Choose the Right RMM Software: Selecting the right RMM software is crucial. Consider your specific requirements, budget, and the size and complexity of your IT environment. Research different RMM solutions and compare features, pricing, and user reviews.
Setting Up and Configuring the Software
Once you’ve chosen the RMM software, you need to set it up and configure it to meet your specific needs. This process involves installing the software, defining access controls, and configuring monitoring and management policies.
- Installation and Configuration: Install the RMM software on your central server or cloud platform. Follow the vendor’s instructions and ensure the software is properly configured to communicate with your devices and network.
- Define Access Controls: Establish user roles and permissions to ensure secure access to the RMM software. Different users may require different levels of access, depending on their responsibilities. For example, IT administrators may have full access, while end-users might only have access to specific features.
- Configure Monitoring and Management Policies: Configure monitoring and management policies to automate tasks and proactively address potential issues. These policies can include automated patching, software updates, security checks, and performance monitoring.
Integrating RMM Software with Existing IT Infrastructure
Integrating RMM software with your existing IT infrastructure is crucial for seamless operation. This integration involves connecting the software to your network, devices, and existing management tools.
- Network Integration: Configure the RMM software to connect to your network and communicate with devices. This may involve setting up firewall rules, configuring VPN connections, or using existing network management tools.
- Device Integration: Install agents on all devices you want to monitor and manage. These agents allow the RMM software to collect data, perform tasks, and interact with the devices.
- Integration with Existing Tools: If you have existing IT management tools, such as Active Directory or ticketing systems, consider integrating them with the RMM software. This integration can streamline workflows and improve overall IT management.
Best Practices for Using Remote Monitoring & Management Software
Remote monitoring and management (RMM) software offers numerous benefits for businesses of all sizes. However, to fully leverage the capabilities of RMM software and maximize its impact, it is crucial to adopt best practices for its effective utilization. These best practices ensure optimal performance, security, and overall efficiency of your IT infrastructure.
Regular Monitoring and Proactive Maintenance
Regular monitoring and proactive maintenance are essential for identifying and addressing potential issues before they escalate into major problems. By regularly monitoring system performance, security logs, and other critical metrics, you can detect anomalies, troubleshoot issues, and prevent downtime. Proactive maintenance involves scheduling regular updates, patches, and other maintenance tasks to keep your systems running smoothly. This proactive approach minimizes disruptions and maximizes system uptime.
Best Practices for Ensuring Optimal Performance and Security
- Establish Clear Policies and Procedures: Implement comprehensive policies and procedures for using RMM software. These should cover access control, data security, incident response, and other critical aspects. Clearly define roles and responsibilities for different team members, ensuring that everyone understands their responsibilities.
- Configure Security Settings: Configure the RMM software’s security settings to align with your organization’s security policies. This includes setting strong passwords, enabling two-factor authentication, and restricting access to sensitive data. Regularly review and update security settings to ensure they remain effective.
- Regularly Update Software: Keep the RMM software, as well as the operating systems and applications it manages, updated with the latest security patches and bug fixes. Software updates often include security enhancements that address vulnerabilities and improve system stability.
- Implement Strong Password Policies: Enforce strong password policies for all users who access the RMM software. Encourage users to create complex passwords that are difficult to guess and regularly change them.
- Use Multi-Factor Authentication: Enable multi-factor authentication for all users who access the RMM software. This adds an extra layer of security by requiring users to provide multiple forms of identification, such as a password and a one-time code.
- Limit User Permissions: Grant users only the permissions they need to perform their assigned tasks. This principle of least privilege helps to minimize the risk of unauthorized access and data breaches.
- Monitor System Activity: Regularly monitor system activity for suspicious behavior. This includes tracking user logins, file access patterns, and network traffic. Use the RMM software’s built-in reporting and alerting features to identify potential threats and respond promptly.
- Perform Regular Backups: Implement a comprehensive backup strategy to protect your data from loss or corruption. The RMM software can be used to automate backups and ensure that critical data is regularly backed up to a secure location.
- Conduct Security Audits: Regularly conduct security audits to assess the effectiveness of your RMM software and security measures. This involves evaluating your security policies, access controls, and other security settings to identify any vulnerabilities.
- Train Staff on Security Best Practices: Provide regular security training to all staff members who use the RMM software. This training should cover topics such as password security, phishing scams, and data security best practices.
Case Studies of Successful Remote Monitoring & Management Software Implementation
Real-world examples of businesses that have successfully implemented remote monitoring and management (RMM) software showcase the transformative power of this technology. By delving into these case studies, we can gain valuable insights into the challenges faced, solutions implemented, and lessons learned.
Successful RMM Implementation in a Healthcare Organization
This case study focuses on a large healthcare organization that implemented RMM software to manage its vast network of medical devices and patient data.
The organization faced several challenges, including:
- Managing a complex and diverse IT infrastructure with various devices and operating systems.
- Ensuring the security and compliance of patient data.
- Maintaining uptime and performance of critical medical devices.
- Reducing operational costs associated with IT support.
The organization implemented RMM software to address these challenges. The software enabled them to:
- Centrally monitor and manage all devices, including medical equipment.
- Automate security updates and patch management.
- Proactively identify and resolve potential issues before they impacted patient care.
- Reduce the number of onsite IT support visits, saving time and resources.
The implementation of RMM software resulted in significant benefits for the healthcare organization:
- Improved security and compliance of patient data.
- Enhanced uptime and performance of critical medical devices.
- Reduced operational costs and increased IT efficiency.
- Improved patient care and satisfaction.
“The implementation of RMM software has been a game-changer for our organization. It has enabled us to improve our security posture, enhance the reliability of our medical devices, and provide better care to our patients.” – IT Director, Healthcare Organization
RMM Software for a Growing Retail Chain
This case study focuses on a rapidly expanding retail chain that implemented RMM software to manage its growing network of stores.
The retail chain faced challenges such as:
- Managing a distributed IT infrastructure across multiple locations.
- Ensuring consistent performance of point-of-sale (POS) systems.
- Maintaining security and compliance of sensitive customer data.
- Providing timely IT support to all locations.
The retail chain implemented RMM software to:
- Centrally monitor and manage all devices across its store network.
- Automate security updates and patch management.
- Proactively identify and resolve issues with POS systems.
- Provide remote IT support to all locations, reducing the need for onsite visits.
The implementation of RMM software resulted in:
- Improved performance and reliability of POS systems.
- Enhanced security and compliance of customer data.
- Reduced operational costs associated with IT support.
- Improved customer satisfaction due to faster and more efficient IT support.
“RMM software has been instrumental in our ability to scale our IT infrastructure as we expand our retail chain. It has enabled us to provide consistent and reliable IT support to all our locations, while reducing our operational costs.” – CIO, Retail Chain
Future Trends in Remote Monitoring & Management Software
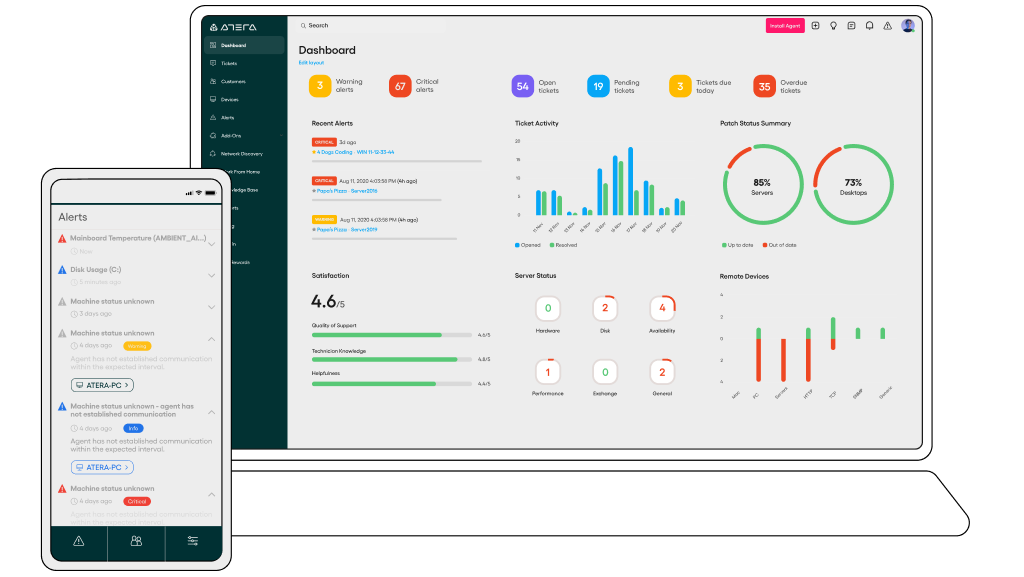
The field of remote monitoring and management (RMM) software is constantly evolving, driven by advancements in technology and changing business needs. Several emerging trends are shaping the future of RMM, promising to deliver even greater efficiency, security, and automation for businesses of all sizes.
Integration with Artificial Intelligence (AI) and Machine Learning (ML)
AI and ML are transforming various industries, and RMM is no exception. These technologies are being incorporated into RMM solutions to enhance automation, proactive maintenance, and security.
- Predictive Maintenance: AI algorithms can analyze historical data from devices and networks to predict potential issues before they occur. This allows IT teams to proactively address problems, minimizing downtime and reducing maintenance costs.
- Automated Threat Detection: ML algorithms can detect and respond to security threats in real-time, identifying suspicious activity and blocking malicious attacks. This helps to improve security posture and reduce the risk of data breaches.
- Performance Optimization: AI-powered tools can analyze system performance data and identify bottlenecks or inefficiencies. This helps to optimize resource utilization and improve overall system performance.
Cloud-Based RMM Solutions
Cloud computing has become ubiquitous, and RMM software is increasingly being offered as cloud-based solutions. This offers several advantages:
- Scalability and Flexibility: Cloud-based RMM solutions can easily scale up or down to meet changing business needs. This eliminates the need for on-premises infrastructure and reduces upfront costs.
- Accessibility: IT professionals can access and manage devices from anywhere with an internet connection. This enhances remote work capabilities and improves collaboration.
- Simplified Management: Cloud-based solutions often come with built-in features for managing updates, security patches, and backups. This simplifies administration and reduces the workload for IT teams.
Focus on Cybersecurity
As cyber threats become more sophisticated, RMM software is evolving to offer comprehensive cybersecurity solutions.
- Endpoint Security: RMM solutions are integrating endpoint security features, such as real-time threat detection, malware protection, and vulnerability scanning. This helps to protect devices from attacks and data breaches.
- Security Information and Event Management (SIEM): RMM solutions are incorporating SIEM capabilities to centralize security logging and analysis. This allows IT teams to identify security incidents and respond effectively.
- Compliance and Auditing: RMM software is being developed to help businesses meet compliance requirements. This includes features for auditing system configurations, monitoring user activity, and generating reports.
Integration with Other IT Tools
Modern RMM solutions are designed to integrate seamlessly with other IT tools, creating a unified platform for managing IT infrastructure.
- IT Service Management (ITSM): Integration with ITSM tools allows for automated incident ticketing, problem resolution, and change management.
- Monitoring and Alerting Tools: Integration with monitoring and alerting tools provides real-time visibility into system performance and alerts IT teams to potential issues.
- Collaboration Platforms: Integration with collaboration platforms allows for better communication and coordination among IT team members.
Last Recap
As businesses continue to embrace digital transformation, remote monitoring and management software will play an increasingly vital role in maintaining a secure, efficient, and scalable IT infrastructure. By adopting the right software and implementing best practices, organizations can unlock the full potential of this technology and gain a competitive advantage in today’s dynamic business landscape.
Remote monitoring and management software empowers you to oversee your systems from anywhere, ensuring optimal performance and security. For those working with web development, setting up a local environment with xampp download is a crucial step. XAMPP provides a convenient package for Apache, MySQL, PHP, and Perl, allowing you to test your web applications locally before deploying them.
This streamlined process helps you effectively manage your projects, ensuring seamless integration with your remote monitoring and management solutions.
