Solution RMM, or Remote Monitoring and Management, is a game-changer for businesses of all sizes. By seamlessly integrating technology and automation, RMM solutions empower IT teams to proactively manage and secure their systems, ultimately enhancing efficiency and minimizing downtime.
Table of Contents
Imagine a world where IT issues are detected and resolved before they impact your business. RMM makes this vision a reality by offering a centralized platform to monitor, manage, and automate critical IT tasks. This powerful tool helps you gain valuable insights into your network’s health, identify potential vulnerabilities, and even anticipate future problems before they arise.
Choosing the Right RMM Solution: Solution Rmm
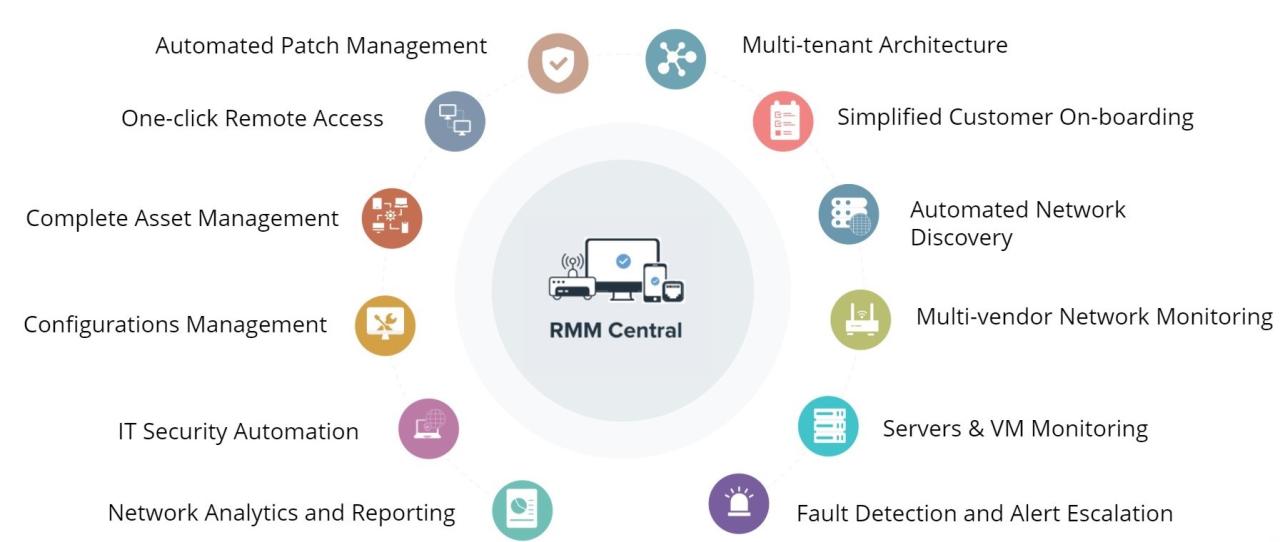
Choosing the right RMM solution is crucial for businesses of all sizes, as it can significantly impact their IT security, efficiency, and overall performance. Selecting the right RMM solution involves careful consideration of various factors, including the specific needs of your business, the features offered by different providers, and the overall cost-effectiveness of the solution.
Key Factors to Consider
The key factors to consider when selecting an RMM solution can be broadly categorized into four main areas:
- Business Needs: The first step is to identify the specific needs of your business. What are your top priorities in terms of IT security, efficiency, and management? Are you looking for a solution that can help you automate tasks, manage patches, or monitor your network? Understanding your specific requirements will help you narrow down your search and focus on solutions that meet your needs.
- Features and Functionalities: Once you know your business needs, you can start evaluating the features and functionalities offered by different RMM providers. Some of the key features to look for include:
- Remote Access: This allows you to access and control devices remotely, which is essential for troubleshooting and managing IT infrastructure.
- Patch Management: This helps you keep your systems up-to-date with the latest security patches, reducing your vulnerability to attacks.
- Endpoint Security: This feature provides protection against malware and other threats, ensuring your devices are secure.
- Asset Management: This helps you track and manage all your IT assets, including hardware, software, and licenses.
- Reporting and Analytics: This provides you with valuable insights into your IT environment, allowing you to identify trends and make informed decisions.
- Automation: This feature can automate many tasks, such as software updates, backups, and security checks, freeing up your IT team to focus on more strategic initiatives.
- Cost and Value: The cost of an RMM solution can vary significantly depending on the features offered and the number of devices managed. It is important to evaluate the value proposition of different solutions and choose one that offers the best balance of features, functionality, and affordability. Consider the long-term costs, including ongoing maintenance and support fees, when making your decision.
- Ease of Use and Support: The RMM solution you choose should be easy to use and provide adequate support. Look for a solution with a user-friendly interface and comprehensive documentation. Consider the availability of customer support, including phone, email, and online chat, and the responsiveness of the support team.
Checklist of Features and Functionalities
When evaluating RMM software, it is helpful to have a checklist of features and functionalities to consider. Here is a comprehensive checklist:
- Remote Access and Control:
- Ability to access and control devices remotely, including desktops, laptops, servers, and mobile devices.
- Secure remote access protocols, such as SSH, RDP, and VNC.
- Session recording and logging for audit and compliance purposes.
- Patch Management:
- Automated patch scanning and deployment for operating systems, applications, and other software.
- Patch scheduling and prioritization based on risk and criticality.
- Patch approval workflows and reporting.
- Endpoint Security:
- Real-time threat detection and prevention, including antivirus, anti-malware, and anti-spyware protection.
- Endpoint vulnerability scanning and remediation.
- Data loss prevention (DLP) capabilities.
- Endpoint hardening and security policy enforcement.
- Asset Management:
- Inventory management of hardware, software, and licenses.
- Automated asset discovery and tracking.
- Software license compliance monitoring.
- Hardware and software lifecycle management.
- Network Monitoring and Management:
- Network performance monitoring and troubleshooting.
- Network device configuration and management.
- Network security monitoring and intrusion detection.
- Backup and Recovery:
- Automated data backup and recovery for critical systems and data.
- Data backup scheduling and retention policies.
- Disaster recovery planning and testing.
- Reporting and Analytics:
- Comprehensive reporting on IT infrastructure, security, and performance.
- Customizable dashboards and reports.
- Data visualization and trend analysis.
- Alerting and notifications for critical events.
- Automation:
- Automated tasks, such as software updates, backups, and security checks.
- Workflow automation and scripting.
- Integration with other IT tools and systems.
- Security and Compliance:
- Compliance with industry standards, such as HIPAA, PCI DSS, and GDPR.
- Data encryption and security protocols.
- Audit trails and logging.
- User Management and Permissions:
- User account management and permissions.
- Role-based access control (RBAC).
- Multi-factor authentication (MFA).
- Integrations:
- Integration with other IT tools and systems, such as ticketing systems, monitoring tools, and cloud platforms.
- API access for custom integrations.
- Support and Documentation:
- Comprehensive documentation and online resources.
- Responsive customer support, including phone, email, and chat.
- Training and onboarding services.
Tips for Conducting a Thorough Evaluation
To ensure you choose the right RMM solution, it is essential to conduct a thorough evaluation of different providers. Here are some tips for conducting a comprehensive evaluation:
- Request a Demo: Request a demo from each provider to see the RMM solution in action. This will give you a better understanding of the user interface, features, and functionality. Pay attention to the ease of use, the responsiveness of the interface, and the overall user experience.
- Read Reviews and Case Studies: Read reviews and case studies from other businesses that have used the RMM solution. This will give you insights into the strengths and weaknesses of the solution from a real-world perspective. Look for reviews from businesses similar in size and industry to yours, as their experiences will be more relevant.
- Compare Pricing and Value: Compare the pricing of different RMM solutions and evaluate the value proposition of each. Consider the features offered, the number of devices managed, and the ongoing support costs. Choose a solution that offers the best balance of features, functionality, and affordability.
- Consider Your Future Needs: Think about your future IT needs and choose a solution that can scale with your business. Consider the flexibility and scalability of the solution, as well as its ability to integrate with other IT tools and systems.
- Get a Free Trial: Many RMM providers offer free trials, allowing you to test the solution in your own environment. This is a great opportunity to evaluate the solution’s features, functionality, and ease of use before making a commitment.
- Ask Questions: Don’t hesitate to ask questions about the RMM solution. Ask about the provider’s security practices, support policies, and future roadmap. This will help you understand the provider’s commitment to security, customer service, and innovation.
RMM Best Practices

Implementing and managing an RMM solution effectively is crucial for maximizing its benefits and ensuring optimal IT performance. By adhering to best practices, organizations can streamline operations, enhance security, and improve overall efficiency. This section delves into strategies for optimizing RMM performance and maximizing its benefits, as well as recommendations for training and support for IT staff using RMM software.
Implementing and Managing an RMM Solution
Successful implementation and management of an RMM solution require a well-defined strategy that encompasses various aspects.
Solution RMM is a powerful tool for managing and securing your IT infrastructure. One of its many advantages is its ability to automate tasks, such as downloading and converting YouTube videos to MP3 format using a service like youtube downloader mp3.
This integration helps streamline workflows and ensures consistent results, ultimately enhancing your overall IT efficiency.
- Define Clear Goals and Objectives: Before implementing an RMM solution, clearly define the goals and objectives you want to achieve. This includes identifying specific pain points, such as vulnerability management, patch management, or remote access, that the RMM solution will address.
- Choose the Right RMM Solution: Selecting the appropriate RMM solution is paramount. Consider factors such as the size of your organization, the complexity of your IT infrastructure, and your budget. Evaluate different RMM solutions based on features, integrations, and ease of use.
- Develop a Comprehensive Deployment Plan: A well-structured deployment plan Artikels the steps involved in implementing the RMM solution, including hardware and software requirements, user training, and communication strategies. This plan ensures a smooth transition and minimizes disruptions.
- Establish Clear Roles and Responsibilities: Define roles and responsibilities for managing the RMM solution, including who will be responsible for configuring, monitoring, and troubleshooting. This helps ensure accountability and effective utilization of the solution.
- Implement Strong Security Measures: RMM solutions handle sensitive data, so it is essential to implement robust security measures. This includes using strong passwords, enabling two-factor authentication, and regularly updating the RMM software.
- Monitor and Evaluate Performance: Regularly monitor the performance of the RMM solution to identify areas for improvement. Track key metrics such as patch deployment rates, security vulnerability resolution times, and user satisfaction.
Optimizing RMM Performance
Optimizing RMM performance is essential for maximizing its benefits and ensuring efficient operations.
- Regularly Update the RMM Software: Keep the RMM software updated to benefit from new features, security patches, and bug fixes. Regular updates ensure the software operates efficiently and securely.
- Automate Repetitive Tasks: Leverage the automation capabilities of the RMM solution to streamline tasks such as patch management, software deployment, and endpoint security checks. Automation reduces manual effort and improves efficiency.
- Configure Alerts and Notifications: Set up alerts and notifications for critical events, such as security breaches, system failures, or software updates. This ensures timely intervention and reduces downtime.
- Optimize Reporting and Analytics: Utilize the reporting and analytics features of the RMM solution to gain insights into IT performance, identify trends, and make data-driven decisions.
- Implement Best Practices for Endpoint Management: Ensure that endpoints are configured and managed according to best practices. This includes implementing strong password policies, enabling disk encryption, and using endpoint detection and response (EDR) solutions.
Training and Support for IT Staff, Solution rmm
Providing adequate training and support for IT staff is crucial for maximizing the effectiveness of the RMM solution.
- Offer Comprehensive Training Programs: Conduct comprehensive training programs to familiarize IT staff with the RMM solution’s features, functionalities, and best practices. This includes hands-on exercises and real-world scenarios.
- Provide Ongoing Support: Offer ongoing support through documentation, FAQs, online forums, or dedicated support channels. This ensures that IT staff have access to assistance when needed.
- Encourage Continuous Learning: Encourage IT staff to stay up-to-date with the latest RMM best practices and security threats by attending webinars, conferences, or online courses.
The Future of RMM
The RMM industry is constantly evolving, driven by advancements in technology and the ever-changing needs of IT professionals. This evolution is shaping the future of RMM solutions, leading to innovative approaches and new opportunities for MSPs and IT departments.
The Impact of Artificial Intelligence and Machine Learning
AI and ML are transforming the way RMM solutions operate, offering significant benefits for both MSPs and their clients. These technologies can automate tasks, improve efficiency, and provide valuable insights that enhance decision-making.
- Automated Patching and Vulnerability Management: AI-powered RMM solutions can analyze systems for vulnerabilities and automatically apply patches, reducing the risk of security breaches and minimizing downtime. For example, an RMM solution can automatically identify and patch known vulnerabilities in a network of devices, ensuring a proactive security posture.
- Predictive Maintenance: By analyzing historical data and system performance metrics, AI can predict potential hardware failures before they occur. This allows IT professionals to proactively schedule maintenance, minimizing downtime and reducing unexpected costs. For example, an RMM solution can predict when a hard drive is nearing failure, allowing IT professionals to replace it before it causes data loss.
- Enhanced Security Monitoring: AI-powered security monitoring can detect anomalies and suspicious activities in real-time, providing faster threat detection and response. For example, an RMM solution can use AI to identify unusual network traffic patterns or unusual user activity, alerting IT professionals to potential security threats.
Closing Summary
In conclusion, Solution RMM empowers businesses to achieve new levels of IT efficiency, security, and reliability. By leveraging the power of automation, proactive monitoring, and intelligent insights, RMM solutions streamline operations, optimize performance, and ultimately contribute to a more productive and secure business environment. Whether you’re a small startup or a large enterprise, implementing a robust RMM solution can be a strategic investment that yields significant long-term benefits.
